Discover the world of Industrial Control Systems with an attack mindset! We will follow a hands-on approach, growing from a very simple local process to a realistic ICS environment with 3 words in mind:
- Build: how does it work?
- Break: what are the weaknesses and how to exploit it?
- Secure: what can we do to fix it?
Day 1 & 2 will allow you to discover and understand ICS and its components, by creating your own training environment and programming it. We’ll spend day 3 attacking a realistic ICS environment, and on day 4 we’ll learn how to secure it.
Moreover, the training doesn’t stop on the last day! Each participant will receive a 30-day access to the “ICS cybersecurity academy” elearning portal, which allows to watch the training content in video, as well as perform all the exercises on a cloud platform.
The first two days will allow you to get a good understanding of Industrial Control Systems, its main components, and how they work together. Moreover, you’ll create & program your own ICS training kit by programming a software PLC and connecting it to a SCADA server that you’ll configure.
The third day will be dedicated to an engaging end-to-end attack on a realistic ICS environment: you’ll start by attacking a corporate network, pivot to the ICS network and then try to disrupt an industrial process!
On the last day, we’ll introduce the main standards for ICS cybersecurity, with a heavy focus on IEC 62443. We’ll review common architectures, then we’ll move on a to a case study, in which we’ll perform a security analysis of the ICS environment you attacked on day 3: identifying weaknesses and associated risks, then identifying and prioritizing possible recommendations.
Moreover, the training doesn’t stop on the last day! Each participant will receive a 30-day access to the “ICS cybersecurity academy” elearning portal, which allows to watch the training content in video, as well as perform all the exercises on a cloud platform.
The outline of the training is the following:
DAY 1
- Introduction to Industrial Control Systems
- Automation basics & programming PLC
- ICS protocols
- Hacking the process
- Focus on PLC security
DAY 2
- Process supervision: SCADA and DCS
- Linking to corporate environments: Windows & Active Directory security
- SCADA/DCS specific vulnerabilities
- An introduction to safety
- Industry 4.0 & IIoT
DAY 3
- Day-long Capture the Flag
DAY 4
- ICS cybersecurity general approach & standards
- Focus on ICS architectures
- Case study: improving the security of the ICS from the CTF
An video introduction to the elearning version of this training can be a quick way to learn more about the training:
Detailed content
Below is the full description of each module:
[BUILD] Introduction to ICS
Objectives for attendees
- Understand a standard ICS architecture and the different components
- Understand how ICS is different from IT, but also how it’s similar
Content
- A brief history of ICS
- Vocabulary
- The CIM model
- Classic architectures
- ICS components (PLCs, HMI, SCADA, DCS, sensors, RTUs, Historian, etc) and their roles
- OT vs IT
- Common ICS vulnerabilities
[BUILD] Automation basics & programming PLC
Objectives for attendees
- Understand the concepts of automation
- Learn ladder logic programming
Contents
- Introduction to automation (PID loop…)
- Basic steps of programming a PLC
- LAB: programming several examples in Ladder & SFC using soMachineBasic from Schneider and deploying it to the PLC simulator (70% of the module is hands-on)
[BUILD/BREAK] ICS protocols
Objectives for attendees
- Get familiar with some of the most common ICS protocols
- Understand the different types of protocols and when to use them
- Be able to analyze a packet capture using Wireshark
- Get familiar with Modbus, OPC-UA… clients to exchange data with PLCs and simulators
Contents
- General presentation of ICS protocols (fieldbus, supervision, data exchange)
- LAB: exercises on analysis of network packet capture (modbus/tcp, S7, OPC-UA)
- LAB: Exchange data with the PLC simulator using modbus clients, S7 as well as OPC-UA client
[BREAK] Hacking the process
Objectives for attendees
- Understand that having a negative impact on the process doesn’t stop at getting admin on a few Windows boxes and sending some Modbus commands
Contents
- Short discussion on the difficulties of hacking a real process and presentation of research work on the topic (“easy button for cyber-physical ICS attacks” by Reid Wightman, “Rocking the pocket book: hacking chemical plants for competition and extortion” by Marina Krotofil).
- Introduction to MITRE ATT&CK and focus on the last steps of the attack (Inhibit Response Function, Impair Process Control, and the possible outcomes)
[BREAK] Focus on PLC security
Objectives for attendees
- Understand the hardware & software components of a PLC
- Learn about the standard services usually found on PLCs and how to abuse them
- Understand how PLC manufacturers use specific protocols for engineering/administration
- Understand how those specific protocols could be used in real attacks
Contents
- Presentation of PLCs internal architecture
- Discussion about OS and middleware (codesys)
- Presentation of vulnerabilities on standard interfaces (web, ftp, snmp…)
- LAB: Identify & exploit exposed interfaces on the PLC simulator
- Presentation of Modbus 90 function used by Schneider PLCs
- LAB: Use of specific exploits against Schneider simulators
[BUILD] Process supervision: SCADA & DCS
Objectives for attendees
- Understand the link between PLCs/Controllers and the SCADA/DCS
- Understand the differences between SCADA and DCS systems
Contents
- General presentation on supervision systems (SCADA & DCS)
- LAB: Programming a SCADA software (Schneider IGSS) to interact with the PLC simulator (80% of the module is hands-on)
[BREAK] Linking to corporate environments: Windows & Active Directory security
Objectives for students
- Understand the security challenges of Windows
- Understand Active Directory, its credential management, and associated risks
Contents
- Presentation of Windows
- Introduction to Active Directory
- Credential management in Active Directory (NTLM, Kerberos..)
- LAB: Exploiting a Windows vulnerability with Metasploit
- LAB: Gathering credentials and pivoting to other systems
- LAB: Gathering information from Active Directory (users, computers…)
80% of the module is hands-on
[BREAK] SCADA/DCS specific vulnerabilities
Objectives for attendees
- Discover the most common vulnerabilities to look for in SCADA/DCS software
Contents
- Description of common DCS/SCADA vulnerabilities
- LAB: Gathering interesting data from SCADA project files
- LAB: Bypassing the access control features because of poor file permission
[SECURE] An introduction to safety
Objectives for attendees
- Understand that there are several layers of protection to prevent major incidents
- Understand the need for cybersecurity in Safety Instrumented Systems (SIS)
Contents
- Presentation of layers of safety, including SIS, physical safety…
- Presentation of safety analysis methods and link to cybersecurity (SPR: Security PHA review)
- LAB: Performing a SPR on a simplified HAZOP analysis of the distillation process
[BUILD] Industry 4.0 & IIoT
Objectives for attendees
- Discover the technologies behind the “Industry 4.0 buzzword”
- Understand the associated security challenges
Contents
- Industry 4.0 genesis & use cases
- Industry 4.0 technologies
- Industry 4.0 & IIot communications protocols (LoRa, Sigfox, MQTT…)
- LAB: Analysis of a MQTT network capture
- LAB: MQTT pentest
[BREAK] CTF
Objectives for students
- This module takes the whole 3rd day
- Practice the newly acquired skills on an end-to-end attack on ICS
Contents
- There is really no “content” in this module, 0 slides
- Attendees connect to a specific CTF and must find a way to impact the physical process.
- This CTF is guided, meaning that I’m here to help anyone who needs it and I will give some hints to make sure everyone gets a chance to complete the most of the CTF challenges by the end of the day
- A CTFd server will be used to monitor progress and guide students
- The setup is composed of:
- Virtual machines part of a corporate Windows Active Directory environment
- Virtual machines part of an ICS network (servers, HMIs…)
- Real and virtualized PLCs (7 real PLCs from Schneider & Siemens)
- A physical setup connected to the PLCs: a model train and two robotic arms
Below is a short video of the CTF livestream on Twitch :
All attendees will receive a write-up of the CTF after the training.
- In order to accommodate remote training, I already have an online version of the CTF, using PLC simulators and a custom-developed “physical process”, that can be reached through a VPN or directly from a web browser! I will host the attendee’s virtual machines in the cloud and allow access through a “Guacamole” server, that provides RDP or VNC access through a simple web server.
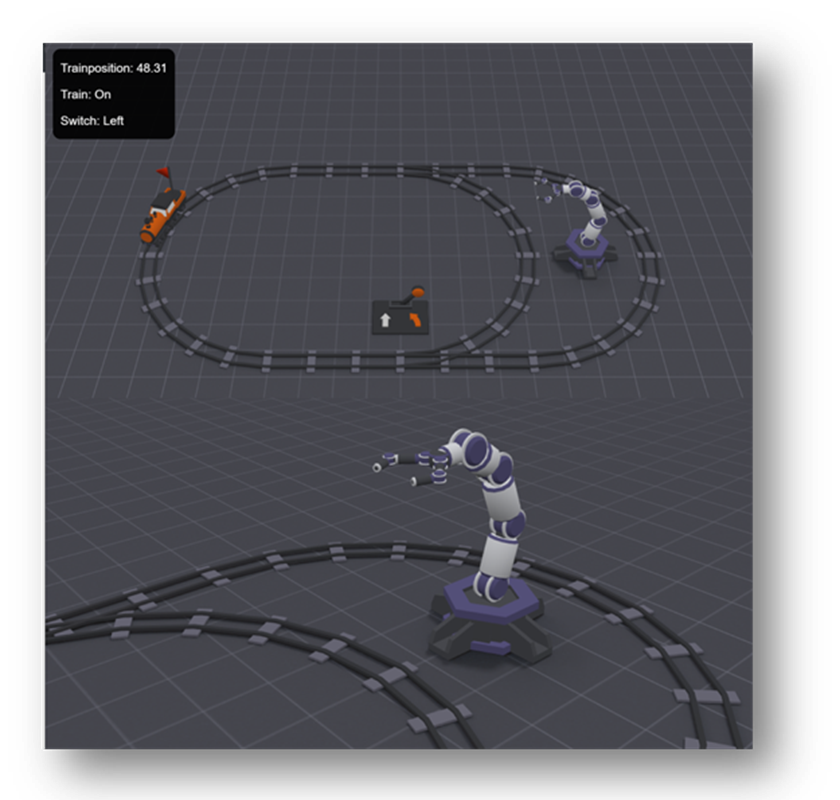
“Virtual” equivalent to the hardware CTF
If the training happens “on-site”, attendees will work on the cloud CTF and then will be given access to the physical one to test their attacks on real hardware!
For more information on the elearning portal, please take a look at the website: https://ics-cybersecurity.academy/next-trainings/online-training/
[SECURE] ICS cybersecurity general approach & standards
Objectives for attendees
- Understand that no new technology is a silver bullet and that we need start with the basics
- Discover the leading standards for ICS cybersecurity
- Get some feedback from projects I have worked on for clients
Contents
- Overview on ICS cybersecurity standards
- Large focus on IEC62443 (cybersecurity lifecycle, zones & conduits, security levels..)
- Main topics to consider (governance, hardening…) and open discussions on the difficulties and how to overcome it)
[SECURE] Focus on ICS architectures
Objectives for attendees
- Understand the common architectures
- Understand that data exchange with the corporate network and third parties is necessary
- Learn the best practices for IT/OT network segmentation
Contents
- Discuss the common ICS architectures and the associated security challenges
- Large focus on network segmentation possibilities (based on NIST SP800-82)
- Focus on data diodes
[SECURE] Case study: improving the security of the ICS from the CTF
Objectives for attendees
- Work on a realistic case study to secure an ICS environment
- Collectively challenge each other’s ideas
Contents
- Analysis of the documentation on the case study (organization description, network diagrams, firewall rules, …)
- Use of IEC 62443 approach to define security zones & conduits
- Definition of an action plan and open discussion on the technical & organizational challenges to implement it

Greetings, I would be interested in taking the course in a virtualized environment. so that classes can be done 100% online
LikeLike
Hello, thank you for your interest. At the moment, we do not offer this class remotely. However, we’re working on a new version of the training that might be done online, I will post more information once the content is more advanced.
LikeLike
Hello Anthony, the training is now available online, take a look at https://pentesting-ics.com/next-trainings/online-training/ and feel free to send me an email at contact@pentesting-ics.com for any question!
LikeLike
Hi,
Do you have any online version of this course currently available for taking? If so, can you provide some details on it.
Thanks
LikeLike
Hello! The online version of the training is almost finished!
I recorded all the content in video, and now I’m migrating the CTF to the cloud, I’ll contact you in one to two weeks!
LikeLike
Cool thank you.
LikeLike
Hello, the online training is available, you can find more information at https://pentesting-ics.com/next-trainings/online-training/
Let me know if you have any question!
Best regards,
Arnaud
LikeLike